In the modern era of the digital world, life has become more convenient. Different digital devices working with the internet have developed. Seamless integration of digital devices has revolutionized the world. It greatly impacts how we work, live, and communicate.
With every technological advancement comes a downside; the digital world is facing the risk of cyber threats. As more people are using online platforms, the security risk has increased. Both individuals and businesses are vulnerable to cyber threats.
The ratio of cyber threats will increase in the coming years, and hence, global spending will also increase. Gartner, a famous technology research center, predicts that by 2026, cybersecurity funding will surpass $260 billion globally. People should be more concerned about cyber threats.
In this article, I will explore the different cyber threats and how you can prevent your business from them.
Let’s start!
What are Cyber Threats?
A cyber threat, commonly known as a cybersecurity attack, is defined as a malicious act of stealing or damaging data or digital well-being. Anything that can cause serious harm to computer systems or networks is a cyber threat. It can range from data breaches, computer viruses, and denial of service. Cyber threats include different types of viruses, trojans, and hacking activities.

There are three types of cyber threats that usually damage users:
- Damage the data: It includes corrupting, deleting, or altering file information.
- Data theft: It includes theft of sensitive information, which leads to security concerns.
- Disturbing service: The whole network is disturbed in this case. It causes inactivity at work
7 Common Cyber Threats for Business
Cyber threats are so dangerous that they can shut down the whole system. It can result in electrical breakout, military equipment failure or violate government national security.
These are some cyber threats to be aware of:
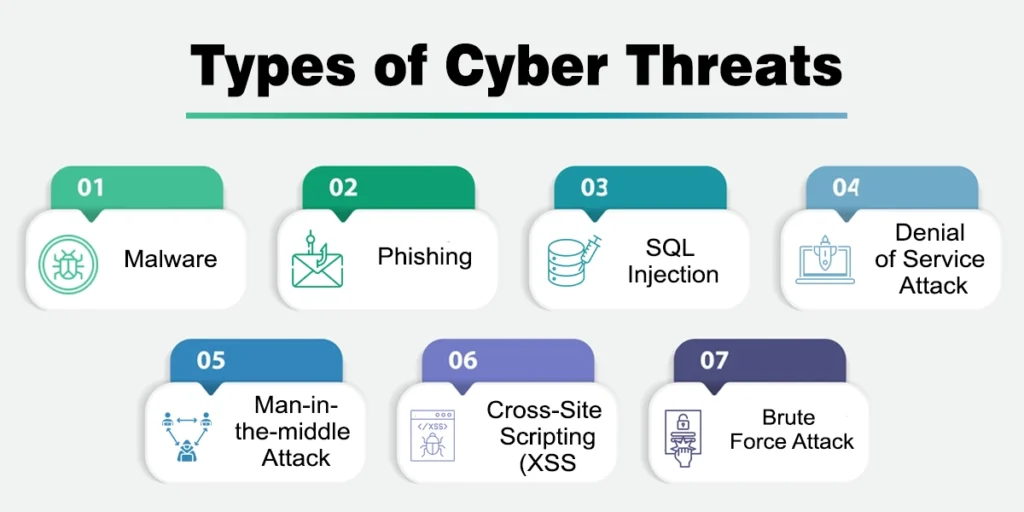
1. Malware
Malware is a common name everyone must have heard. It is designed to harm computer systems, networks, and devices. Various types of malware are famous
- Viruses: These are self-replicating programs attached to some executable file. It can be termed an infected file. It can erase data and corrupt files, causing system instability.
- Worms: Worms are more threatening than viruses. They can propagate independently across networks. These worms attack the operating system or application to spread rapidly. WannaCry is a good example of older Windows systems.
- Trojans: This malware can steal data or install other software
- Spyware: It acts like a spy to collect sensitive information like browsing, login history, and personal data. People use spyware for advertising or corporate competition.
- Adware: Adware displays unwanted advertisements and often comes with free software. This unnecessary software can intrude and slow down another system.
2. Phishing
It is a cyber threat attempt where hackers appear to be legal entities to deceive individuals. Phishing targets people who share sensitive information such as usernames, passwords, or financial details.
These attacks can be seen through fraudulent emails, fake websites, and instant messages. It insists that users click on malicious links or download infected attachments.
3. SQL Injection
As it is named, it is a cyber attack on the database to take control of your data. The technique is used to steal data. With SQL (structured language query) injection, attackers create vulnerabilities in data-driven applications by inserting malicious code in the form of SQL statements.
4. Denial of service attack
The primary purpose of a Denial of Service (DoS) cyber attack is to overwhelm a system. It causes a slowdown of the server, system, or network with excessive requests.
A more severe option of DoS is DDoS. It is a distributed denial-of-service attack where multiple computers are attacked. Financial institutions, online services, and e-commerce platforms suffer more from this kind of cyber threat.
5. Man-in-the-middle attack
It acts like a middle-person attacker between two people. It is a cyber threat where a cybercriminal intercepts secretly between two communicators to steal or alter data.
Once an attacker gets into the conversation, they can steal personal data and sensitive information
6. Cross-Site Scripting(XSS)
It is a cyber attack on the website where the attacker injects malicious scripts that appear on the browser of the user. Cross-site scripting works by causing a vulnerable website to return malicious JavaScript to users. When the malicious code executes inside the victim’s browser, the attacker has complete control over their interaction with the program. There are three types of XSS.
- Stored XSS: HA armful script is stored on a targeted server in the comment section or forum post. Every website visitor can see it.
- Reflected XSS: In this type of XSS, the attacker embeds a malicious script in the URL and tricks the victim into executing it by offering a link. It is not stored on the server side.
- DOM-based XSS: This cyber attack makes the client-side vulnerable to loading a malicious script. It works on manipulating the DOM( Document Object Model) structure of the website.
7. Brute Force Attack
A brute force attack is a hacking technique that involves trial and error to crack passwords, login credentials, and encryption keys. It is a simple but effective method of gaining unauthorized access to individual accounts as well as systems and networks within corporations.
The cyber attack is named brute as it excessively attempts to gain access to user accounts. It has five different types
- Simple brute force: Hackers manually crack login details.
- Dictionary attack: The attacker chooses a victim and then checks different potential passwords against that person’s username.
- Hybrid brute force: The Attacker tries to crack the password using the username and adding a combination of numbers, years, or random characters.
- Reverse Brute Force Attack: The process begins with a known password. The attacker uses weak passwords to match login details in the database.
- Credential stuffing: The attacker works on an already stolen username and password. Try these details to crack their other accounts on social media.
How to Protect Your Business from Cyber Attacks?
You can take different steps when implementing cybersecurity for the business. Follow these five steps to protect your business in 2025:
Consistent Risk Assessment
Consult a cyber security expert within the IT field to evaluate security risk assessment.
Only cyber experts know how and where the data of your employees, clients, customers and investors is saved. In case of loss, where is the backup, and what do you do for its protection?
You might not know the company is vulnerable to cyber-attacks. Only regular assessment determines gaps in internal and external cyber security processes. Protect your data from cyber breaches and keep up to date with the best cyber security industry practices.
Third-Party Risk Management
Companies should not only focus on internal cyber security measures but also focus on controlling cyber security risks from third parties. Third-party risk includes potential threats and dangers from suppliers, traders, vendors, and external partners associated with the business. They can have access to your computer and networks.
To prevent third-party potential cyber security risks, research external companies’ security measures before parenting with them. Keep communication clear with them about keeping your data secure first.
Create Strong Passwords and Access Control
Weak passwords are the most common cyber security risk businesses face. To counter this issue, encourage employees to create strong passwords and be careful about their access. Here are a few tips, according to Google, that you can use to create a strong password:
- Use at least 12 characters long or 14 for better security
- A combination of uppercase, lowercase letters, numbers, and symbols should be used
- Don’t use a person’s name or organization’s name
- Make it different from the previous password
- Make it easy to remember but difficult to guess.
Use Updated Cyber security Software
Companies should use updated cyber security software to protect themselves from cyber threats. This software protects the system from viruses and cyber-attacks. Keep in mind these points about cyber security software to protect company data
- Update regularly: Make sure to use an updated version of the software, as it contains security patches to fix vulnerabilities that hackers can attack.
- Enable automatic update: Allow devices in your organization to receive security updates and automatically install them in the system. This is the easiest way to keep the system healthy and free from cyber attacks. Nothing has to be done manually.
- Check for the new version: If a new version is available, install it as it can fix more issues.
- Use multi-layer protection: Enable all features of security tools like antivirus, anti-malware, firewall, and threat detection systems. This will enhance network security.
- Choose reputable vendors: Purchase cyber security software from a trusted vendor who can give updates and fix later issues.
Train Employees on Cyber Security Risk
Implement cyber security practices in your business. One of them is to educate employees about potential cyber threats and how they affect clients and business operations. Tell them how to avoid potential threats, like how phishing emails look or how to create strong passwords.
- Schedule training sessions with employee information on common cyber threats. Take a few quizzes to create interactive elements.
- Use posters and internal communication highlighting key security practices
- Spread cyber security risk awareness among employees.
Conclusion
Cyber threats are a battlefield for businesses on the front lines. Instead of reacting to attacks, businesses should work on implementing cyber security practices. Spread information about common cyber threats like malware, phishing, and denial of service. Businesses can prevent potential cybersecurity risks by regularly conducting cyber risk assessments with IT experts and updating their security software.
Protection from cyber threats ensures uninterrupted business operations for long-term stability and growth. Arm your business today with knowledge and tools not just to survive but also to thrive in facing tomorrow’s cyber challenges.

